The banking and financial services industry is subject to some of today’s most demanding regulations and oversight due to the value of its data, regular auditing, and the penalties and economic repercussions of malfeasance. In the digital age, staying ahead in the banking game depends on technology platforms, processes, and policies that ensure your organization’s compliance and security. Above all, identity and access management solutions form the backbone of this necessary technology infrastructure.
What is Identity Management? – A Brief Overview
Identity and Access Management (IAM) is the umbrella term for the structures and processes within any organization that administer and manage its employees’ access to resources and data.
At their most distilled, IAM solutions and policies manage the centralization, connection, and governing of access to your systems, data, and resources. Think of them as the brains that oversee an organization’s IT environment. Centralizing identity information for each individual preserves their associated permissions and security to drive and facilitate automated processes. Standardizing and synchronizing your organization’s IAM establishes the creation of an accurate, easily managed database facilitating secure, proper access for all users.
IAM solutions help calibrate the perfect sweet spot between too-open access and too-rigid security for each user’s specific role within your organization’s unique environment and operations. A successful implementation provides you with the management tools for IT resources and business processes. This ensures the right users have the right access to the right resources, right at their fingertips, regardless of where their role takes them.
A more in-depth explanation of IAM here.
The Rise of IAM in Banking (and Healthcare)
IAM is not a banking-specific solution, but the strategies and technologies have been adopted within the financial sector more than most. Banks and financial services were some of the first to see their largest organizations adopt official IAM policies and technologies alongside healthcare. This is primarily due to the increased regulations overseeing these industries dating back roughly 30 years, beginning with then-President Bill Clinton’s signing of the Health Insurance Portability and Accountability Act (HIPAA) in 1996. The regulation that kicked off the increased oversight in the financial services sector was 1999’s Gramm-Leach-Bliley Act (GLBA), shortly followed by 2002’s passing of Sarbanes-Oxley (SOX).
- HIPAA: “The Health Insurance Portability and Accountability Act (HIPAA) was created primarily to modernize the flow of healthcare information, stipulate how Personally Identifiable Information maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft, and to address limitations on healthcare insurance coverage – such as portability and the coverage of individuals with pre-existing conditions.”
- GLBA: While primarily repealing part of 1933’s Glass-Steagall Act, GLBA included “The Financial Privacy Rule”, which required institutions to inform their clients at the beginning of the consumer relationship and annually thereafter of the data collected about the individual, where it is stored, how it is used, and how it is protected (15 U.S.C. §§ 6801–6809).
- SOX: Following scandals including Enron and WorldCom, SOX was enacted to oversee the verification of financial records, the mandating and increased independence of regular 3rd party auditing, and general corporate transparency and accountability.
As a result of the regulations, the active enforcement of “Segregation of Duties” became much more important. Segregation of Duties (SoD) refers to the discipline that enforces operational checks and balances. SoD controls the execution of various processes, preventing potentially compromising positions for employees. SoD often separates a process and its verification or enforcement. These controls may distribute various aspects of a process amongst employees or business units. They may require multiple authorizations. A government’s separation of those who pass, verify, and enforce laws serves as an example.
SoD Examples
Examples of business processes that utilize SoD include:
- Separating an asset custodian from the asset’s record keeper
- Separation of financial advisory from mergers, acquisitions, and insider news related to the advising firm
- Employees can’t write their own reimbursement checks or execute their own purchase orders
- Project managers must review and sign off on their team’s work or documentation
- Hiring staff may not set compensation levels
- Different employees must be responsible for ordering inventory as those who verify and enter the received goods into inventory systems
With Great Data Comes Great Responsibility
Information systems and data heavily influence all aspects of modern life and banking is no exception. If anything, the banks and financial services hold much more of our individual Personally Identifiable Information (PII) than the average organization. As such, regulations and their enforcement will increasingly focus on IT resources as more and more business processes rely on technology. Data collection, storage, and access are now mission-critical. Some of the most important technological processes and policies that IAM controls in any organization are user account lifecycle management, and access governance.
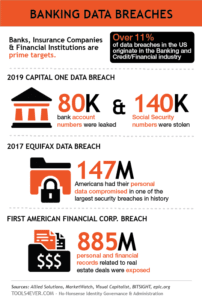
Regardless of industry, size, or location, most modern organizations require informational technology resources to complete daily functions: an HR System for employee information; accounting and payroll software; local or cloud storage for file and data sharing, and so on. Effectively utilizing these resources amidst today’s expectations of immediacy necessitates supporting instant (and compliant) access to apps, files, and data – at any time, from any device, in any location. However, the never-ending onslaught of malicious digital entities in a world more connected than ever complicates traditional access assignments and methods. When over 11% of data breaches in the US originate in the banking and credit/financial industry, security is as much of a concern as compliance.
User Account Lifecycle Management
The “User Account Lifecycle” defines the collective management processes for every user account. These processes can be broken down into Creation, Review/Update, and Deactivation. If your bank or financial service utilizes IT resources of any kind, you rely on user accounts to access them.
This lifecycle begins with account creation and resource provisioning stages on an employee’s first day. That user must be provisioned with all of their resources to hit the ground running. Setting up all of a user’s accounts and permissions manually can take days, weeks, or more. From that point on, access rights must be regularly reviewed to maintain a streamlined, compliant network.
Access Governance and Role-Based Access Control
IAM solutions enforcing Access Governance (AG) or Role-Based Access Control (RBAC) determine access rights according to the configuration for a given user’s job role. Access to the resources that each role requires is configured in AG and RBAC. These configurations enforce restrictions so that users are not able to access resources and data they don’t need for their job. The configurations for each role must still be maintained as time goes on, however. Unnecessary access is merely a compliance violation, malfeasance, instance of human error, or an incentive for fraud waiting to happen.
Permissions and group memberships typically determine access rights to various folders and shares within the network. You wouldn’t want every customer to have unrestricted access to a cabinet containing each other’s bank account or credit information. Similarly, you wouldn’t want those same files stored on the network without protection. Network permissions and group memberships are assigned based upon job role and the different levels within the file system’s hierarchical structure.
AG and RBAC are the internal IT controls that separate responsibilities to prevent fraud and minimize temptation or mistakes. Blackmail and coercion are particular concerns for employees with important roles or that handle valuable data – especially so in the banking sector.
Without access restrictions, the originally provided SoD examples are susceptible to the following:
- Improper or fraudulent use of a company asset
- Insider trading
- Employees could fraudulently route funds to themselves
- Employees editing their own work may not catch a mistake or may be able to abuse noncompliant access
- Hiring staff may offer a friend a position or inflated compensation over other applicants
- An employee could create and cover-up an order discrepancy to take goods for themselves
Privileged vs. Regular Accounts
Privileged accounts are those within your network that have higher levels of access rights and permissions. When roles requiring elevated permissions (e.g. directors, managers, specialty roles), conduct operations through their privileged accounts all the time, there is a much higher likelihood of those accounts becoming unsecure and excessive activity may be carried out without notice. Privileged access management is critical to keeping your environment secure. If it’s not necessary to use a privileged account, don’t. It’s that simple. On the opposite end, generic accounts shared by multiple users eliminate insight.
User Account Deactivation
When a user departs an organization, all of their associated accounts must be deactivated and de-provisioned. Security risks are the more obvious reason for following deactivation procedures. A malicious ex-employee can take sensitive data (e.g. client information, intellectual property, account credentials) or damage your environment in worst-case scenarios. Ex-employees may access your IT resources until deactivation – for days, weeks, months, or years. Stalled deactivation is especially dangerous for cloud-hosted resources that can be accessed by ex-employees from anywhere.
The other primary reason for adhering to a standard deactivation process is to prevent the accumulation of “orphaned accounts”. Orphaned accounts are those no longer associated with an active user and remain in your environment. This digital detritus clutters your ability to accurately assess your environment while also taking up storage space. Further, should your organization be successfully attacked by a malicious intruder, orphaned accounts make perfect camouflage for them.
All About Access
The data and resources that employees (or ex-employees) may access directly affects compliance with the Financial Privacy Rule of GLBA. If your bank or financial service remains responsible for notifying clients about what happens with their data, you need to know what is going on internally to communicate and demonstrate such. With banking’s digital transformation, access methods and user identities serve as primary audit trails or the “smoking gun”. Unfortunately for banks and financial services, their data breaches or mishandlings correlate to giving up so much of a customer’s real-life identity is compromised.
IAM isn’t just a stamp of approval to show your customers once per year, however. Proper management of the user account lifecycle sets up your bank or financial service for optimal audit preparation and minimizes data breach risk levels. With SOX, the rigorous audit standards have never been higher. Utilizing an IAM solution to help manage your bank or financial service’s back-end processes means that every activity by every user is logged in the system. When it comes time for internal audit preparations or for a 3rd party to turn over every rock during their investigation, those activity reports and audit trails allow you to ensure your organization is compliant and then prove it.
Manually managed network environments are incredibly messy and even the most knowledgeable administrator can suffer from blind spots. Going into an audit without IAM access records is the equivalent of handing your financial records over as a couple of paper bags stuffed with years of non-itemized receipts.
Multi-Factor Authentication
When it comes to IAM, one of the easiest security measures an organization can adopt is the addition of Multi-Factor Authentication (MFA). MFA requires the user to enter a pin code, respond to a push notification, or complete another measure following the successful entry of username and password credentials. Without completing the MFA process, the user can’t log in or access IT resources or data. MFA greatly assists security measures as it provides an extra layer without being a burden on the end-user.
People already use MFA processes to regularly prove their identities outside of IT scenarios. For example, an ATM card requires a personal identification number (PIN). Authentication only occurs when both the card and PIN are used in conjunction; the methods do not authenticate anything exclusive of each other. For IT resources, the use of security questions would count as a less-sophisticated MFA policy. Today, MFA can be enforced via One-Time Password (OTP) clients on a mobile phone, push or SMS notifications, or physical security tokens or keys stored on USB or similar devices.
The banking and finance industry seem to be ahead of the curve on consumer-facing MFA. For many digital banking platforms and resources, users are already required to complete an MFA step to access their account. The same motivations for protecting individual clients with MFA applies to the employees of any bank or financial service – there’s just an exponential factor of risk.
IAM – Mission Critical, End User-Friendly
IAM strategies and solutions benefit any organization in the digital age. Sensitive company data, individual clients’ PII, and regulatory compliance make it even more of a necessity for banking and finance organizations. IAM solutions will help centralize and optimize your back-end user processes and access rights to drastically cut down on the administrative effort while enforcing strict security measures to keep your organization safe and compliant. At the same time, all of your users will have immediate access to their IT resources to work efficiently.
__________________________________________________________________________________
John Wilkinson is a technical content writer at Tools4Ever.